
Don't want to miss a thing?
THE SECURITY DEVELOPMENT LIFECYCLE
The Security Development Lifecycle (SDLC), created by Microsoft, is a methodology that enhances code security by incorporating targeted exercises and checks at every stage of development. Initial security recommendations are intentionally broad, addressing a wide range of potential scenarios. From there, each product is assigned a tailored scope of security requirements, policies, and procedures to better defend against specific technological threats.
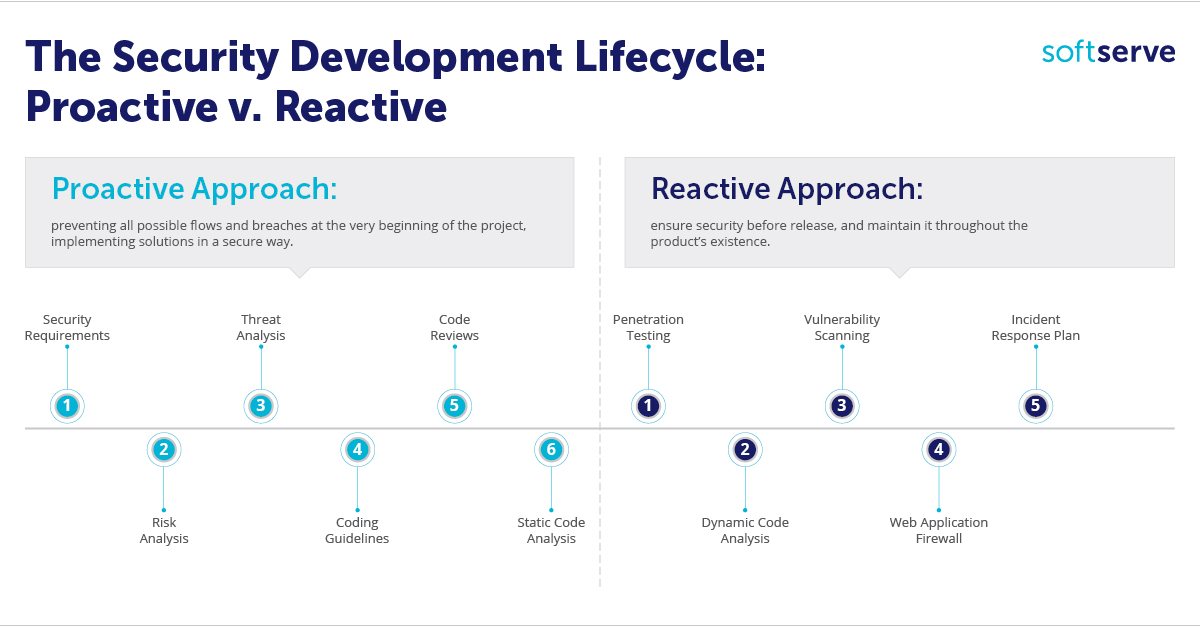
Penetration Testing
One of the most fascinating techniques for a security engineer is conducting penetration testing on an application. This process simulates the actions of a real hacker to uncover security flaws and vulnerabilities, assess authentication and authorization management, validate input, and evaluate many other aspects of the product.
Dynamic Code Analysis
Unlike static analysis, dynamic analysis is performed while the application is running. It continuously monitors functional behavior, response time, system memory, and overall performance. This approach can be integrated into continuous integration workflows, complementing static analysis. While automated tools cannot fully replace human expertise, they significantly accelerate and enhance the work of engineers.
Web Application Firewall
A web application firewall (WAF) is a specialized firewall that operates over the HTTP protocol. It functions as a lightweight version of an intrusion detection system (IDS), but is specifically tailored to HTTP. WAFs enforce rules to protect against common attacks, such as SQL injection and cross-site scripting (XSS). Modern solutions often integrate WAFs with DDoS protection services, providing a dual layer of defense.
Incident Response Plan
UPKEEP AND MAINTENANCE
After the release and throughout the lifecycle of each new version of the product, it is essential to prioritize security maintenance and protocols. While the most challenging security systems are often the newest ones, security engineers and management must implement the response plan and maintain the product environment. This includes regularly updating all tools, libraries, and operating systems in use. Employees should develop a habit of keeping security top of mind, fostering a culture of creating code that is conscious, high-quality, and secure.
Both proactive and reactive approaches are equally important in creating secure environments. While building security from the ground up is ideal, the reactive approach is often necessary to address threats that emerge unexpectedly. The best strategy is to strike a balance between analytical and practical security measures, ensuring your business is protected against a wide range of security threats.
Protect your business with a balanced approach to security. Contact us today to implement tailored SDLC solutions.
Start a conversation with us
