Security risks come in all shapes and sizes, nefarious hacker attacks to disgruntled employees bugging a system to even natural disasters. With all of these unpredictable sources of security risk facing the business world, the best option to mitigate risk is to implement security controls.
What is Security Control
To put it simply, a “security control” is any safeguard that helps to detect, avoid, or minimize security risk. To illustrate the concept of security controls for information systems let's use the comparable example of a Middle Ages castle. The typical castle always had high and wide walls, rounded with a moat, powerful army, and wise authorities that would defend themselves from attackers.
In a modern technological reality, security controls play an important role regulating any company’s daily life. Similar to the castle example, they harden access to internal perimeters using firewalls, anti-spam solutions, antiviruses, network and host intrusion prevention systems, and different analytic tools to make all these things work together. In other words, the purpose of any security control is to mitigate and manage the risk to a company’s digital assets. There are several different approaches to implement controls in informational systems: compliance-based, risk-based, and ad-hoc.
Approaches of Implementation Cybersecurity Controls
;
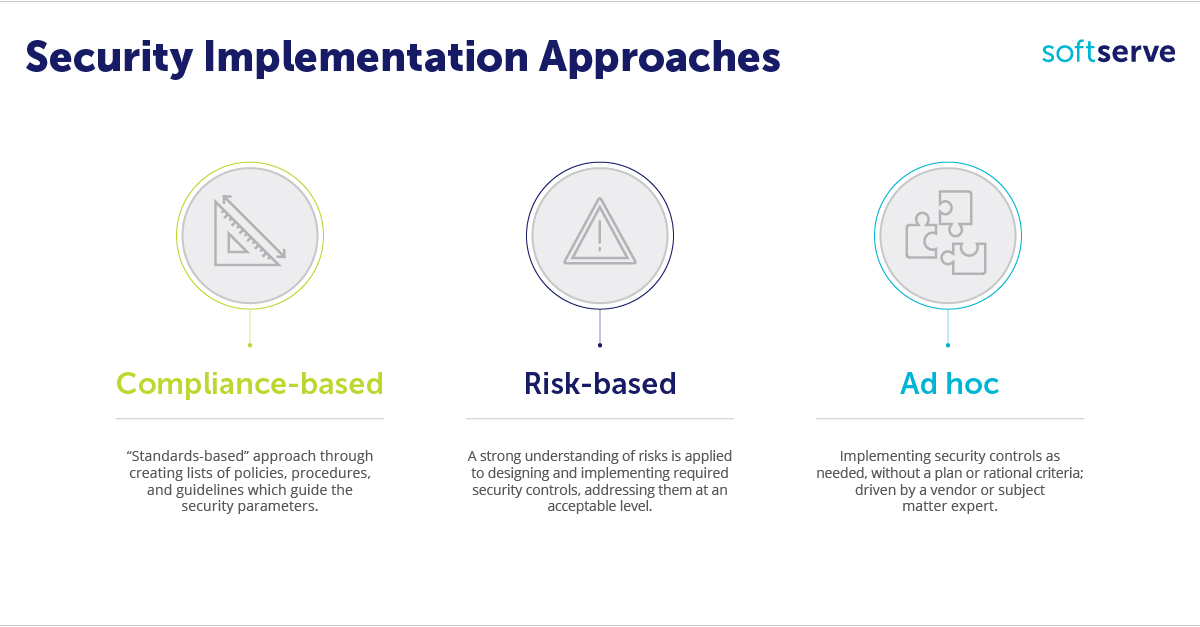
Identity Management
One of the most important things in the information world is identifying who you are working with. In terms of security, this means focusing on managing and provisioning user identity information. This control covers the procedures and processes from hiring a person to retirement. The main idea of identity management is to create standard and centralized processes that cover all possible user changes working within the particular organization. Knowing users allows the company to implement other controls, build correct access rules, and use this information for incident response or different investigations.
Provisioning & De-provisioning
Giving and removing rights is essential for a company from a security perspective, as users often change jobs inside the company and their rights should be changed accordingly. This process could be difficult due to variety of factors, such as a large number of employees, continuous changes in job duties, or complicated and distributed systems. Users may need access to different systems, services, accounts, a nd information, so with changing positions, access to these things should be changed too.
Authorization
The purpose of authorization is for the company or system to be able to differentiate and identify users. The issue of broken authorization is common and harmful, it is even in the OWASP’s Top 10 Apllication Security Risks. The basic recommendation that 100% works is the “least privilege rule.” This means giving as few privileges as possible to perform daily duties, grant extra rights only when required, and revoke immediately after privileges are no longer required. The same rule works with documents: if the user does not have to change something inside it, read-only access is preferred.
Access Control Lists
Access control lists (ACL) are a logical step for providing division of rights between users among the different systems inside the organization. ACL may include single users, groups, and even machines who have permission to use resources on a particular system or machine. The main point is to correctly change, add, or remove permission during the user’s time at the organization. It is important to remember that forgetting to remove old rights may lead to critical information leakage or even data corruption.
Privileged User Management
Privileged users are like gods in the system: they can do everything and anything. Understandably, they require a very conscious attitude and strict control. Commonly used approach towards management privileged account include points like:
- Limiting such accounts only to staff who require it due to job functions
- Carefully logging all things that have been done under admin accounts
- Using stronger passwords or other more complex authentication methods, such as two-factor authentication
- Reviewing the necess ity of privileges for such an account on a regular basis
Change Management
Change management is vital to the IT infrastructure. All changes have to be implemented in the correct order, as larger organizations usually have a complicated structure with different, interrelated services. Minor changes in services could dramatically affect others, which consequently may disrupt the work of hall organization. The change management generally includes some procedures for tracking those changes as well as documents that list the history of the implemented changes.
Configuration Management
It is critically important to maintain the secure configuration of different network devices (such as routers or printers, for example), systems and applications in order to ensure the security of an organization. Security misconfiguration is number five in the OWASP Top Ten Application Security Risks. Owing to the complexity of today’s systems, the process of correct and secure configuration becomes a challenge. In order to simplify and unify these activities, different policies and guidelines must be created and used. The main thing to remember: never use default passwords on any kind of system and turn off all functionality that is not in use. This rule works similar the least privilege approach, but as it applied to programs.
Patch Management
Today, security breaches appear frequently in all kinds of software. To solve this issue and maintain security of their products, vendors provide their customers with freshest fixes: patches. Despite the importance of installing these fixes as soon as possible, patch management procedures should be put in place and followed carefully. Patches should be installed on the test environment and checked thoughtfully before setting up on the production, as they (patches) can cause conflicts with other systems, even other patches, or violate internal policies.
C hecking Controls
One thing to remember while implementing security controls is to actually check and see how they’re working. There is a great variety of tools that check and maintain the work of security controls like SIEM (Security Information and Event Management) systems, IDS (Intrusion Detection Systems), anti-viruses, and WAFs (web application firewalls). Moreover, to test the overall security of the organization, red teaming can be used as an extra check, that will undercover weaknesses and unprotected areas of the particular company.
Interested in how to implement security control in the cloud? Check out our latest whitepaper “Cloud Security and the Containers Approach” by Igor Beliaiev, Security Engineer.


