
Don't want to miss a thing?
Overcoming Firebase SSO Challenges: A Client Success Story
Firebase Authentication offers cloud-based services and libraries for various programming languages, simplifying user authentication and integration with other Firebase tools. It supports industry standards such as OpenID Connect (OIDC) and OAuth 2.0, which makes it easy to connect with backend systems.
However, Firebase doesn’t provide the full functionality of an identity provider or built-in Single Sign-On (SSO) capabilities. Organizations that want to take full advantage of cloud technologies can face integration challenges, especially when multiple systems or domains are involved.
CLIENT CHALLENGE
The client wanted to create a custom SSO solution and had already chosen Firebase, trusting Google’s plan to introduce native SSO support in the future. They preferred not to migrate to other providers such as Auth0 or IdentityServer, as that would require user-password migration and could introduce potential security or compatibility issues. Instead, they opted for a temporary but secure custom approach based on Firebase Authentication.
The client managed several customer portals built on WordPress Customer Relationship Management (CRM) systems. All portals shared the same user base stored in Firebase Authentication. However, users needed to re-enter their credentials every time they visited a new portal or followed a link between them.
Many users didn’t realize they could use the same login for each site, which led to confusion and poor user experience.
By default, Firebase maintains authentication context for a single domain, meaning it doesn’t automatically support SSO across multiple domains. To address this limitation, SoftServe proposed creating a new service that would extend Firebase’s functionality and enable seamless SSO between the client’s portals.
FIREBASE DEFAULT BEHAVIOR
To understand why a custom solution was needed, it’s important to look at how Firebase Authentication works by default.
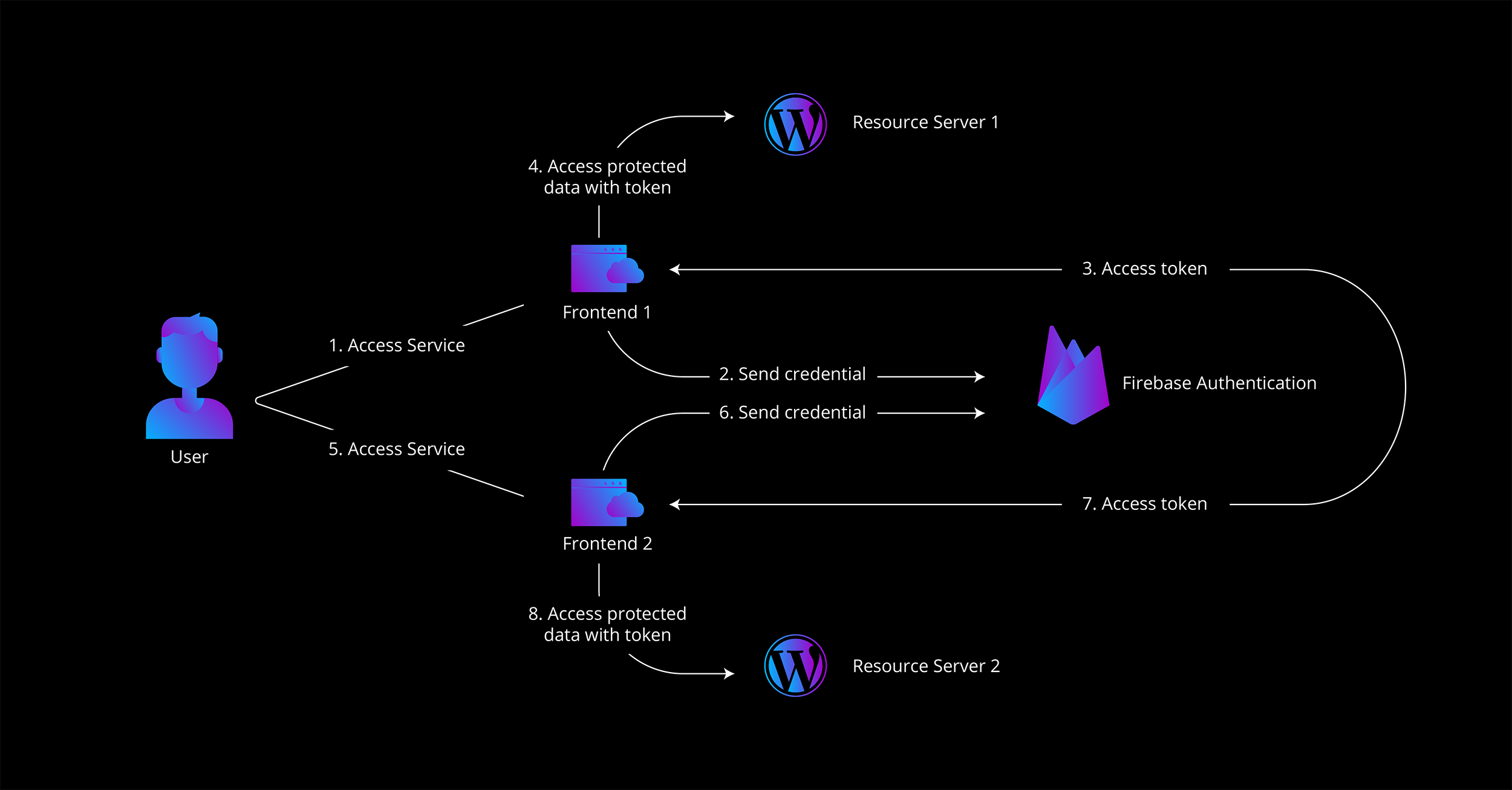
In a typical setup, Firebase handles authentication separately for each domain. When a user tries to access a protected resource, they must log in to that specific domain. After authentication, Firebase issues tokens that allow access to data stored in services such as Cloud Firestore or Cloud Storage.
The general flow looks like this:
- A user accesses a service through a client web application.
- They enter their credentials.
- The authorization server validates them and generates an access token, session cookie, and related Firebase or Google tokens.
- The frontend application then uses this token to request protected data from the resource server.
SCOPE OF WORK
To overcome these limitations, the client’s needs were defined through several key use cases:
- Users should have access to a central portal where they can manage their resources (via REST) according to assigned roles.
- They should be able to log in using either local accounts or social identities.
- Once authenticated, users should be able to access other portals without re-entering credentials.
- The solution should also support service accounts, allowing portals or applications to authorize and access resources on their own behalf.
These use cases shaped the foundation for the SSO solution. After reviewing them, SoftServe determined that OpenID Connect (OIDC) and OAuth 2.0 would provide the most suitable approach for authentication and authorization. Both are widely used standards that support multiple authorization flows, including:
- Implicit grant flow
- Authorization code grant flow
- On-behalf-of flow
- Client credentials grant flow
SOLUTION DESIGN
To enable OpenID support for the client’s WordPress portals, the OpenID Connect plugin was used. This plugin allows user authentication via the OpenID Connect (OIDC) and OAuth 2.0 authorization code grant flow. With this flow, a user’s credentials are never shared directly with the application, only the authorization server validates them.
To prepare the final solution, several components were developed or configured:
Login application – A simple React-based interface for user authorization. When an unauthorized user tries to access a WordPress portal, they are redirected to this standalone login app to provide credentials. It was hosted on Firebase Hosting as a separate project.
Apigee platform – Chosen as the orchestrator for HTTP endpoints and the main authorization service. Apigee provides built-in OAuth 2.0 support and detailed documentation, allowing the creation of custom endpoints for authentication, including:
- oath/authorize – Redirects unauthorized users to the login application.
- oath/token – Exchanges the authorization code for an access token after a successful login.
- oath/verifyToken – Used by the resource server to validate the user’s token.
HOW IT WORKS
The process flow for the new SSO solution looked as follows:
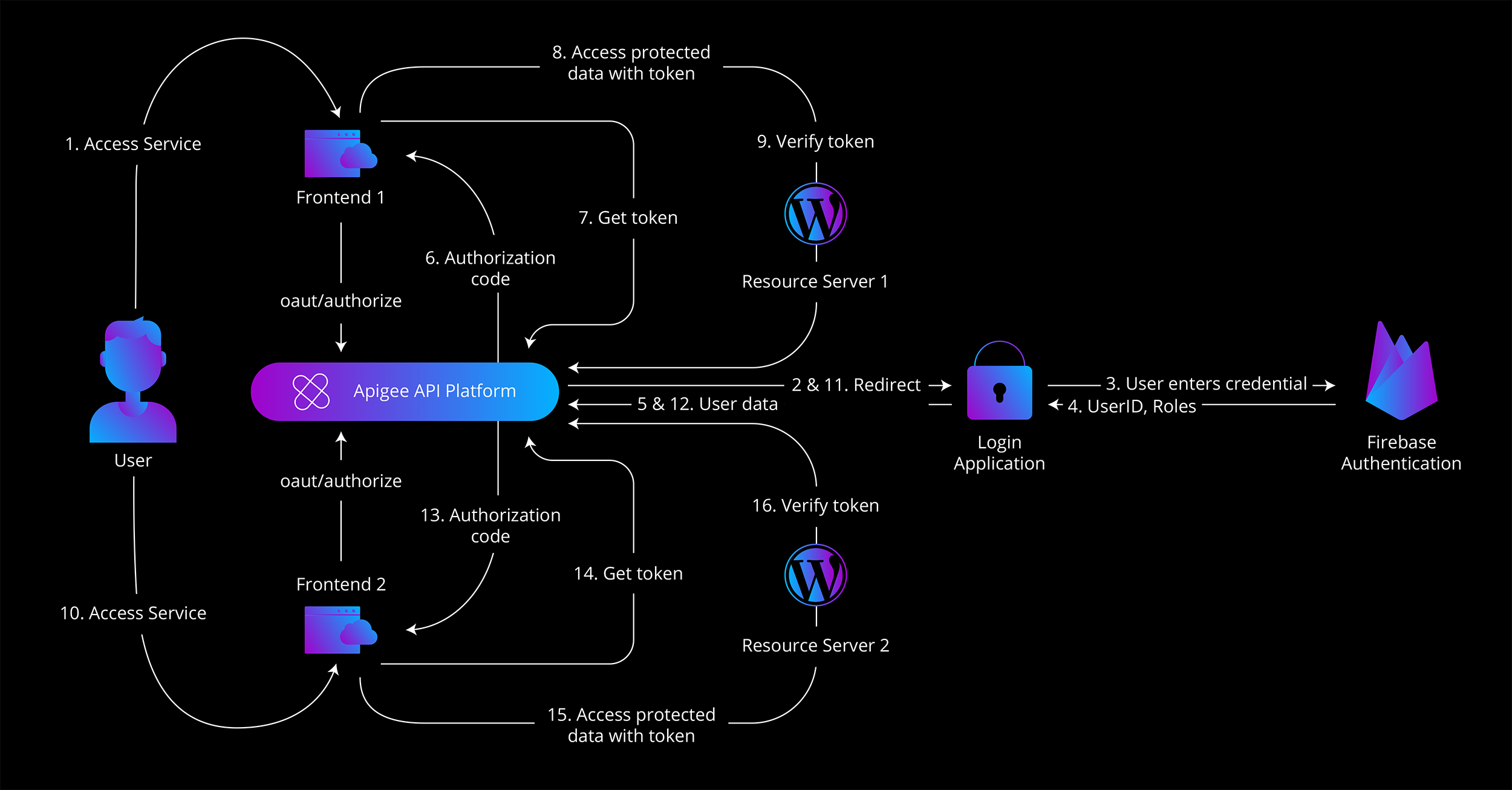
- A user attempts to access a protected website.
- The frontend redirects the unauthorized user to Apigee’s /oauth/authorize endpoint.
- Apigee redirects the user to the Firebase-hosted login application.
- The user enters their credentials and receives their user ID and role information.
- This data is sent back to Apigee, which generates an authorization code and returns it to the frontend.
- The frontend exchanges this code for an authorization token by calling the /oauth/token endpoint.
- Apigee issues the token, which the frontend then uses to access protected resources.
- When the resource server receives a request, it verifies the token through Apigee’s /oauth/verifyToken endpoint.
- When an authorized user visits another site, no additional login is required. The active user session is recognized, and a valid token is provided automatically.
TECHNICAL FLEXIBILITY
The implemented solution was designed with flexibility in mind, allowing it to be extended or adapted for other applications in the future. Even if a custom application does not include its own mechanism for validating tokens on the resource server side, such validation can still be achieved through integration with Firebase Functions and the Firebase Admin SDK.
Using this approach, user roles and permissions can be verified securely through a simple REST call. Apigee can expose an HTTP endpoint to trigger the Firebase Function, which then verifies the user’s token and returns the result to the calling application.
This configuration allows organizations to maintain consistent authorization logic across all connected systems without the need for additional complex development.
SUMMARY
SoftServe delivered a cloud-ready SSO solution that fully met the client’s needs and expectations. The final setup enabled seamless authentication across multiple WordPress portals without requiring user migration to a third-party identity provider.
The project was completed in just three weeks, demonstrating that a complex authentication challenge could be solved quickly and efficiently using existing cloud tools like Firebase and Apigee.
Until Google introduces official SSO support for Firebase, this solution provides organizations with a reliable way to achieve single sign-on functionality while maintaining full control over user data and minimizing development effort.
If your company faces similar integration challenges or needs a custom authentication solution, contact SoftServe. Let’s discuss how we can help you.
Start a conversation with us
