They say with great power comes great responsibility, and that is especially true for the financial institutions that work with consumers’ and investors’ hard-earned money. The financial services, banking, and fintech industries face a unique set of security concerns, and it is up to the business leaders in each of these industries to build a strategy that protects the interests of their stakeholders. Read on for ways to prepare for and prevent harmful security breaches, rather than having to repair and repent with your customers when their worst security nightmares turn into reality.
Passive Detection Methods
Apart from creating your own manual checks for GitHub, Pastebin, HackerNews, and all of the underground hackers forums (or DarkNet), there are two main ways to detect and address hacks: passive and active means. Let’s start with passive methods.
Honeypots
Honeypots and honeynet are security deception technologies installed inside OS to detect, deflect, or counteract attempts of an unauthorized use of information systems. These special vulnerable spying machines run to gather information about the motives and tactics of the black hat community targeting dif ferent networks. “White hats” use these traps (along with production systems with different kinds of agents) to monitor and/or register any activities inside an operating system and catch malicious software such as key-loggers, spyware, and rootkits.
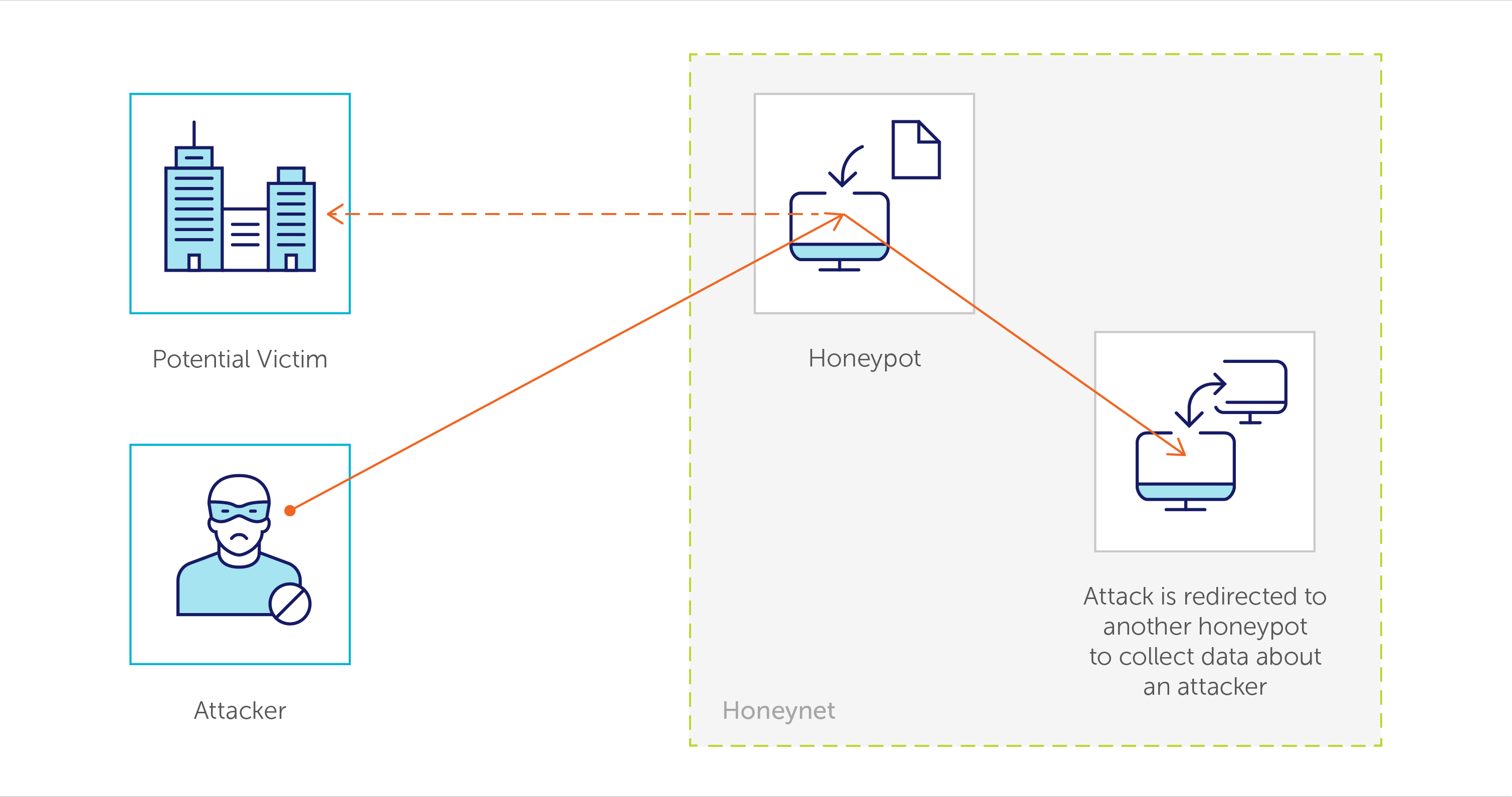
As suggested by their name, honeypots are the sweetest technique to track the newest approaches hackers use to attack any systems demonstrating their skills against your lure. This technology is perfect for collecting information about the latest malware, viruses, DDoS, and 0-days. Honeypot monitoring allows early detecting and blocking attackers and even more – misguiding black hats to wrong targets where it is possible to track and catch them. Checkout this website created by Norse, the global leader in live attack intelligence, that helps companies detect and block cyberattacks, especially from the DarkNet.
Canary Tokens
With canary tokens, you set “traps” with attractive names (like Top_Management_Salary_2017.xlsx) across your network and get notified when any of these files is opened. Since you know that these files are “dummies,” it is a clear indicator that somebody is trying to trespass your resource – be it a hacker or even an employee whose curiosity was triggered by an appealing title.
Threat Intelligence
Companies that provide threat intelligence as a service collect and store information about typically infected machines, regions, and IP addresses with the worst security reputations (i.e., hacked hosts), so the connection established with your network from one of the grey- or black-listed hosts is considered to be suspicious. Remember: Monitoring is your best friend . Big companies should have security information and event management (SIEM) systems – their own or co-managed – to track all information events, correlate them, and detect if there is any anomalous activity. You are your own greatest advocate when it comes to data protection and hackers are waiting for your security grip to loosen up.
For example, if employee John Smith is successfully logging in to Allianz USA network at 3 am after entering the wrong password 10 times, your SIEM systems would report this activity as suspicious. (This is also why every big organization should have established typical users profile.)
Security Operation Centers
Network activity within fintech organizations is usually comprised of multiple systems and related log events. Since one small IT unit is not enough to handle proper monitoring and regular checkups, it is a common practice to outsource work to security operations centers whose responsibility is to monitor and correlate all log events and inform the hiring organization of suspicious or anomalous activity.
Active Detection Methods
The following concepts offer more active detection methods. The best security strategies will use a combination of both.
Monitoring
First, all financial services organizations should make sure their users have security notifications on (similarly to how Google informs about unknown web browsers) with additional security checks in place when users log in from an unusual location or at an unusual time. There should be a person or team who receives such alerts – around the clock – ready to react as necessary, kicking off a formal investigation when activity meets established criteria. Above all, know your weak and risky systems, since every organization has vulnerabilities that can't be patched/secured because of technical issues.
Early Detection
Depending on when a se curity breach has been detected, it is not always wise to repel a hacker right away. When an attack is detected early on, you can actually use a hacker’s presence and activity as an opportunity to collect as much information about how the incident came to pass and potential vulnerabilities (again, threat intelligence or SOCKS-proxy providers can help with this process). Usually, security experts will quickly set up a passive method, like luring hackers into honeypots or other set traps with deceptive names of servers or files for them to access fake data. If a security breach has been detected too late, however, the organization’s focus should be on detaching the hacker(s) from its system as soon as possible and monitor other accounts with increased attention.
Employee Training
There is no better security force than people themselves, which is why increasing user awareness about security essentials and how dreadful the outcomes of private data leakage are should be a top priority for every financial services company. Consider providing regular information security trainings, banning access to working accounts for those who haven’t passed a regular safety and security checkup, and even carrying out penetration tests without users knowing that they are a target. These strategies will help employees understand and appreciate the sensitive nature of the information they work with on the job.
Looking for more insights about fintech and financial services? Check out SoftServe’s ebook that explores the technology driving global startup success stories such as Wealthfront, WePay, Circle, and Fidor Bank.

